Telecommunication
Mobile Device Security Certification (MDSCert)
Consult our experts. We are happy to support you.
The GSMA Mobile Device Security Certification (MDSCert) Scheme establishes a framework for assessing and certifying the security capabilities of consumer mobile devices. By adhering to standardized security requirements, mobile device vendors can demonstrate their commitment to protecting users against cyber threats. The scheme provides an independent, structured evaluation process, ensuring that devices meet the necessary security requirements before reaching mobile device consumers.
Mobile devices are evaluated against the relevant GSMA MDSCert Security Requirements, which are based on the ETSI Consumer Mobile Device Protection Profile (ETSI TS 103 732 series).
The MDSCert Scheme defines a set of security requirements:
- Cryptography
- Updates
- Preloaded applications and permissions
- Authentication
- User and privacy settings
- Device integrity
- Connectivity
- Vulnerability remediation and patching
- Device lifecycle
- Device bootloader
- Device security configuration
- OTA client and updates
- Device signing keys
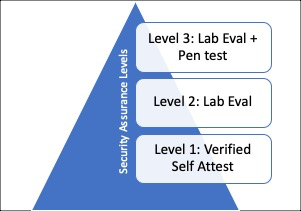
The MDSCert Scheme also defines three security assurance levels:
- Security Assurance Level 1 (Verified Self-Assessment)
- Security Assurance Level 2 (Functional Test + Documentation Review)
- Security Assurance Level 3 (Level 2 + Penetration Test)
What atsec offers:
atsec is an authorized lab for performing Mobile Device Evaluations under the TrustCB scheme. MDSCert scheme evaluations involve four key stages:
1. Preparation Stage
During this stage, the Mobile Device Manufacturer:
- Selects the device(s) for evaluation and the desired Security Assurance Level.
- Submits an application form to TrustCB to initiate the process.
- For higher assurance levels (Level 2/Level 3), coordinates a timeline for evaluation activities with the lab.
2. Submission Stage
The Mobile Device Manufacturer prepares and submits the required documentation and evidence to the lab, including:
- A completed questionnaire.
- Additional evidence and documentation based on the targeted Security Assurance Level.
- Security certificates for relevant components or the entire product.
- Justifications for product similarities and historical certification evidence for reuse.
- For Level 2/Level 3, physical product samples for testing.
3. Evaluation Stage
The lab conducts a detailed evaluation based on the targeted Security Assurance Level:
- Reviews the questionnaire for completeness and accuracy.
- For Level 2/Level 3, performs functional testing on physical devices to validate Mobile Device Manufacturer claims and reviews documentation to verify non-technical requirements (e.g., security lifecycle).
- For Level 3, conducts penetration testing to evaluate resistance to basic attack potential (AVA_VAN.2).
- Prepares and reports results according to the MDSCert Product Evaluation Methodology (FS.55).
4. Certification Stage
TrustCB reviews the evaluation results and the testing methods applied by the lab. Upon approval, TrustCB prepares a Certification Report including the Certification Result (pass or fail), which is delivered to the Mobile Device Manufacturer and the lab.
Why our services are important to you:
atsec’s MDSCert portfolio encompasses the entirety of the MDSCert certification process. We provide the following services:
- Conducting product evaluations at security assurance level Level 1 – Level 3
- Performing a readiness assessment to estimate the level of effort required to successfully comply with MDSCert evaluation

Still have questions?
Can’t find what you’re looking for? Let’s talk!
Common Criteria Evaluation
The Common Criteria (CC), also known as ISO 15408, is an internationally recognized standard used to specify and assess the security of IT products.
Cryptographic Algorithm Testing
Testing that cryptographic algorithms are implemented correctly is a prerequisite for FIPS 140-3 cryptographic module testing and NIAP Common Criteria evaluations.
FIPS 140-3 Testing
FIPS 140-3 specifies requirements related to securely designing and implementing cryptographic modules, and compliance is increasingly mandatory worldwide.
The Information Security Provider
Read Our Latest Blog Articles
Learn the latest and greatest about information security. You’ll find insights and analyses of recent developments in technology and policy on our blog.
-

atsec’s Experience at the Post-Quantum Cryptography Workshop at the KTH Royal Institute of Technology
The PQC Workshop at the KTH Royal Institute of Technology was a trove of valuable insights.
-

Happy Valentine’s Day
We wish a Happy Valentine’s Day to all our colleagues, customers, suppliers and all their families and loved ones.
-

Catching Up with the Cyber Resiliency Act
It’s been a year since the Cyber Resiliency Act was adopted – what’s happened since then?
