The Information Security Provider
atsec IT Security Blog
News about Common Criteria, FIPS, Conferences
and other topics revolving around IT security.
For a non-paginated list of all of our blog posts, head over to our Blog Archive page.
-

atsec leading in Automated Cryptographic Validation Testing
With the sunset of the Cryptographic Algorithm Validation System (CAVS) at end of June 2020, algorithm testing for NIST and NIAP validations and evaluations must now be performed using the Automated Cryptographic Validation Testing System (ACVTS). The list of issued CAVP certificates using ACVTS (i.e. the certificates prefixed…
-
Bye bye, CAVS tool, old friend…
Dear CAVS Tool, We want to congratulate you on years and years of dedicated service. Without you, algorithm testing would not have been what it is today, and we salute you for staying with us for so long. On June 30th you will finally get your well-deserved retirement.…
-
Congratulations to Qualcomm
One of the rewards of working in the evaluation and testing business is to see our customers succeed and show the results of their efforts. We are always happy to work with organizations who are committed to IT security and want to improve their products and processes for…
-
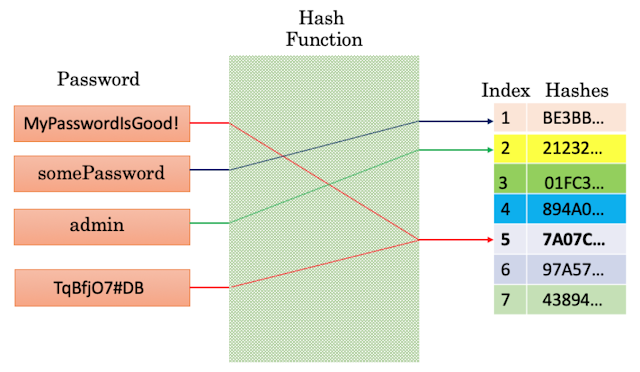
Rise & Fall of MD5
by Richard FantThe RiseMD5 (message digest version 5) was developed in 1991 and is still very popular today, with a wide range of commercial and government applications. MD5 is used to generate hash values of passwords stored on a system as opposed to storing the passwords in plain…
-
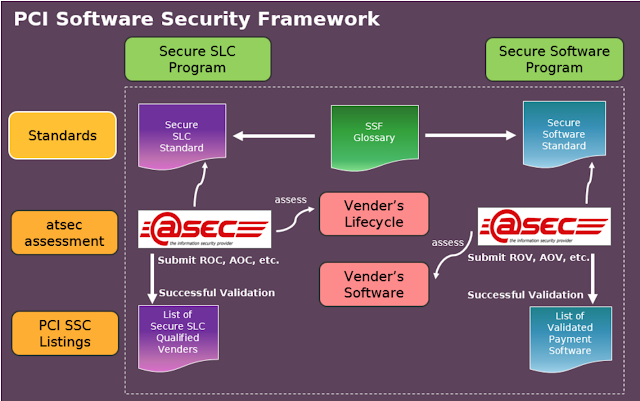
atsec China adds two PCI SSF Assessor Qualifications
atsec China has been qualified by the PCI SSC (Payment Card Industry Security Standards Council) as a Secure Software Lifecycle (SLC) Assessor and Secure Software Assessor company under the PCI Software Security Framework (SSF) program to evaluate a vendor’s software lifecycle and/or validate a vendor’s payment software. The…
-

Data Recycling to Become Mandatory in 2022
According to sources in the DPA (Data Protection Agency) new guidelines will be issued soon that will make digital trash separation mandatory. Every year an estimated 240 zettabytes of re-usable bits are thrown into desktop trash cans. The new guidelines require operating system manufacturers to implement a recycling…
-

Meltdown Attack: 2 Years Later
by Richard Fant Meltdown Attack: 2 years laterIn February 2017, independent security researchers discovered a catastrophic security flaw in the cache design for processors developed by Intel Corporation. After embargoing the information for almost a year while working on a fix, Intel publicly announced in January 2018 the…
-

International Women’s Day
Happy International Women’s Day to all our wonderful atsec colleagues in Europe, US and Asia.